A data breach of some kind seems to be reported every day—many involving major corporations. Table 1on page 39 shows some past data breaches.
In my own state of Oregon, the Employment Department was recently hacked, and as many as 850,000 people were affected. So it’s not just companies that are vulnerable.
For more visualization of data breaches, see the Life is Beau tiful infograph: informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks. If you would like to keep up-to-date on data breaches, I recommend reading Data BreachToday (databreachtoday.com).
Not only do companies have issues, specific software—including some used on almost every computer—has recently been shown to have bugs that could result in data breaches:
- The Heartbleed Bug (heartbleed.com) was a serious vulnerability in the popular OpenSSL cryptographic software library. The weakness allowed stealing protected information, information used to secure the internet. The Bug affected numerous online sites.
- Shellshock (aka Bashdoor) is another piece of open source software which contained bugs that could be exploited. These were discovered in September 2014 and affected more than 500 million servers based
on the Unix operating system. It also affected perhaps billions of other devices such as routers and smartphones.
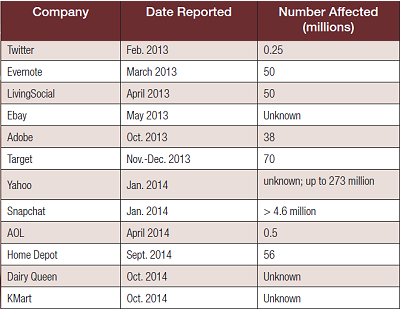 I’ve personally been affected by several of these. Accounts with Target, Home Depot, Evernote, and Twitter led to instances in which I had to take action. Many of these breaches occur at the corporate level, and there’s not much you can do about that. You are always at the mercy of the security protocols of whatever company you are doing business with, whether online or in person.
I’ve personally been affected by several of these. Accounts with Target, Home Depot, Evernote, and Twitter led to instances in which I had to take action. Many of these breaches occur at the corporate level, and there’s not much you can do about that. You are always at the mercy of the security protocols of whatever company you are doing business with, whether online or in person.
With the growing popularity of smartphones and tablets that also require passwords for access, the complexity of password protection becomes more complex. Now, for many people, accessing password-protected sites could involve as many as four devices: a smartphone, a tablet, a laptop computer, and a desktop computer.
One possible solution is OpenID, described by Wikipedia this way: “OpenID is an open standard and decentralized protocol by the non-profit OpenID Foundation that allows users to be authenticated by certain co-operating sites using a third party service.”
You may already have an OpenID and not even know it. Anyone using the following services already has an OpenID: Google, Yahoo, Blogger, Flickr, Myspace, AOL, and others. Facebook stopped using OpenID and now has its own similar service called Facebook Connect.
OpenID allows you to log into another site without having to create an additional password. Just how popular is OpenID? It currently claims more than 1 billion accounts with 50,000-plus websites accepting it.
How Hackers Figure Out Your Password
You may ask how significant these security breach are, especially if you were not directly affected. Hackers use this information to gain insight into how people go about creating passwords. So while your password may not have been compromised, the thought process by which you may have created your password could be. For example, if a system calls for at least one capital letter in a password, most people capitalize the first letter. Other insights such as substituting the number 3 for the letter E or the dollar symbol $ or number 5 for the letter S are also apparent, as well as using the number zero (0) to stand in for the letter O. Data such as this greatly reduces the number of attempts a hacker must make to crack a password. The huge amount of data in the form of revealed passwords and the number of insights revealed allow hackers to crack passwords much more easily than they could before. It is estimated that more than 100 million passwords have been made available publicly for hackers to peruse. This, the availability of cheap hardware in the form of graphics cards, along with free hacking programs, makes hacking much easier than it was just a decade ago. A modern PC along with a graphics card costing a few hundred dollars allows hackers to try, on average, more than 8 billion password combinations per second!
Poor Password Protection
Here are just some of the poor decisions people make when choosing a password:
- 70% use eight characters or less.
- Almost 50% of revealed passwords are duplicates.
- 79% of passwords are in the top 500 list.
- 65% of people write down their passwords.
- 28% use an English word followed by a number, and 66% of those use the number 1.
- Most passwords start with a letter.
- 58% use only lowercase English-alphabet letters
The above details and much more specific information on hackers and passwords are found in two articles from Ars Technica, a noted online resource—“Why Passwords Have Never Been Weaker—And Crackers Have Never Been Stronger” (arstechnica.com/security/2012/08/passwords-under-assault) and “Anatomy of a Hack: How Crackers Ransack Passwords Like ‘Qeadzcwrsfxv1331’”(arstechnica.com/security/2013/05/how-crackers-make-minced-meat-out-of-your-passwords). Another interesting article is from Wired.co.uk—“Anatomy of a Hack: Even Your ‘Complicated’ Password Is Easy to Crack” (wired.co.uk/news/archive/2013-05/28/ password-cracking/viewall).
Software to Store Passwords
One solution to the problem of having numerous passwords is to use software to store them so you don’t have to remember them. The potential downside is that if your master password is compromised, then all your passwords are available. However, if you take precautions, such as having a very secure password, not writing it down anywhere such as a Post-It note in your desk drawer, and not allowing unauthorized people access to any device containing your password-protection software, then you should be fairly safe.
Hints for Creating a More Secure Password
Here are some things to avoid:
- Don’t use whole English words found in any dictionary.
- Don’t use a combination of words such as “horse battery staple” (formerly common advice).
- Don’t use letters clustered on the QWERTY keyboard such as 123qwe.
- Don’t use a word along with simple character substitution such as pa$$word or passw0rd.
- Don’t use words spelled backwards such as drowssap.
- Don’t use a word followed by one or two numbers.
It’s easy to give advice on what not to do, but it’s harder to give suggestions that might actually work. Here are a few pieces of advice for more secure passwords:
- Let the password management software create the password for you.
- Use at least eight characters but preferably 10 or more.
- Begin with a number or special character.
- Use at least one of each of the following: lowercase character, capital letter (and not the first character), numeral (not at the end), and a special character (again not as the last character).
Here’s an example of a fairly secure password for someone born on Sept. 11, 1978, who lives at 119 W. Monroe Street and works as a third grade teacher:
119Tea!3@78Mon
It’s 14 characters, much longer than normal, starts with numerals, not letters, and contains information the user is familiar with.
- The first three numbers are from the street address.
- The next three letters, including a capital letter, are from the person’s profession.
- The next three characters are the grade the person teaches set off by a special character before and after the number.
- The next two numbers are the last two digits of the year of the person’s birth.
- The final three letters are the first three letters of the street the person lives on.
This may not be easy to remember, but it sure beats having your online accounts compromised.
There are sites out there claiming to be able to determine how secure your password is, but beware. Some are likely harvesting passwords. Here are two reliable sites where you can go to check your passwords:
The above password scores 148 and is considered very strong by How Secure Is My Password, and the Password Meter site states it would take a desktop PC 2 billion years to crack!
By far the easiest way to manage your passwords is to use software. There are many possibilities available for all platforms. Here are questions to keep in mind when choosing software:
- Do you need the software to work on multiple devices?
- Are you comfortable housing your passwords remotely, i.e., on the cloud, such as on Dropbox?
- How do you want the passwords stored—locally on your computer, on an encrypted USB device, etc.?
There are a wide variety of password managers for both Windows and Mac computers. Here are two good articles reviewing this category of software: