INTERNET WAVES
Your Password Has Expired and Must Be Changed
By Shirley Duglin Kennedy
It never fails. When I’m under deadline pressure and desperately need to access a journal article, that’s when I run up against the dreaded “Your password has expired” warning. And because I’m using a Department of Defense-related system, the hoop-jumping to select a new, acceptable password is extensive. This is an actual screen grab from the site in question:
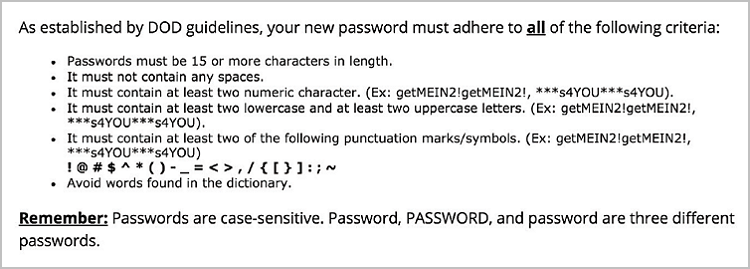
Is it a bit extreme? Maybe. But depending on where you work, it’s also not so unusual. And this is just one site. In this day and age, the average internet user is dealing with a multiplicity of logins. How many depends on whom you ask.
According to an often-quoted study by Microsoft Research, “The average user has 6.5 passwords, each of which is shared across 3.9 different sites. Each user has about 25 accounts that require passwords, and types an average of 8 passwords per day” (research.microsoft.com/en-us/um/people/cormac/papers/www2007.pdf).
Note that this study was published in 2007—almost a decade ago. It’s probably safe to assume that most folks have acquired a much larger array of logins since then. Some more recent estimates include the following:
- The Norwegian Centre for Information Security says that the average minimum number of private passwords per person is 17; the average minimum number of work passwords per person is 8.5 (passwords12.at.ifi.uio.no/NorSIS/NorSIS_Passwords12.pdf).
- A 2012 Janrain/Harris Interactive study says that “58 percent of online adults have five or more unique passwords associated with their online logins and 30 percent of people have more than 10 unique passwords they need to remember. 38 percent of people think it sounds more appealing to tackle household chores—from folding the laundry to scrubbing toilets—than to try and come up with another new user name or password” (bit.ly/1QxCAMp).
- According to a 2014 study by the National Institute of Standards and Technology and the U.S. Department of Commerce, “On average, DOC employees had nine (range: 1 to 400) accounts at work that require logins. Due to the wide range of the data, medians were used for calculating the central tendency. The median of frequently used passwords was five (range: 0 to 105) and the median of occasionally used passwords was four (range: 0 to 245). Further breaking down the number of accounts requiring logins, showed that 21.8 % of the employees had less than or equal to five accounts, 41.5 % had between six to ten accounts, 25.4 % had between 11 to 20 accounts, and 11.0 % had more than 20 accounts” (nvlpubs.nist.gov/nistpubs/ir/2014/NIST.IR.7991.pdf).
123456 x 200
Meanwhile, Dashlane (a company that—surprise—makes a password management application) offers this bit of prognostication: “[T]he number of accounts we use is growing at a 14% rate, meaning it doubles every 5 years. In 2020, the average number of accounts per Internet user will be 207! Are you ready to remember 207 login and password combos?” (blog.dashlane.com/infographic-online-overload-its-worse-than-you-thought).
More password minutia:
Now, if you’re reading this column, you’re likely an information professional or knowledge worker of some sort. The odds are pretty good that you have to manage many more passwords than the average person. And this can be a convoluted process. To begin with, you have to come up with secure passwords. Microsoft offers an online checker that allows you to test the strength of a password (microsoft.com/en-us/security/pc-security/password-checker.aspx).
Then you need some sort of tool or system for keeping track of the passwords so you can retrieve them when needed. Security guru Bruce Schneier discusses several strategies in a relatively brief, nontechnical essay (schneier.com/blog/archives/2014/03/choosing_secure_1.html), and there is actual intelligent discourse and valuable information in the extensive comments section at the end of the piece (although it gets far geekier than Schneier’s advice).
Password Management
One potential solution is using a password management tool. In addition to storing and retrieving your passwords, it will also generate a unique, strong password for every one of your logins. A January 2016 article in The New York Times reviewed three of the most popular of these (nyti.ms/1OGnbpL). Lifehacker reviewed five in January 2015; the comments are fairly worthwhile, with users chronicling their experiences (lifehacker.com/55291 33/five-best-password-managers). PC Magazine ran a broad roundup in February 2016 (pcmag.com/article2/0,2817,2407168,00.asp).
My personal choice is 1Password (agilebits.com/onepassword), because its browser extensions make it simple to use, and it syncs its database of logins easily among my computer and mobile devices. Also, once you buy it, there are no ongoing service charges, as is the case with several of these tools. Most offer some sort of free trial, so you can get a feel for how they work before you ante up.
But even the strongest password will not protect you if potential evildoers get their virtual hands on it—especially if you, similar to so many of us, use the same login at multiple websites. So you may want to consider two-factor (or two-step) authentication, where available. Essentially, this means combining something you know (a password or a PIN) with a second bit of information that verifies your existence. For example, your bank may send you an email or a text message with an additional numeric code that you need to type in to access your account. An extensive list of sites that support two-factor authentication is available at twofactorauth.org. |